Encrypting Sensitive Information: The Digital Safeguard You Can't Ignore Scanning vulnerability cyber seguridad fortinet quadrant challenger gartner practices informationssicherheit política
If you are looking for What is Data Encryption? - Bitdefender Cyberpedia you've visit to the right page. We have 25 Pictures about What is Data Encryption? - Bitdefender Cyberpedia like Data Encryption: Safeguarding Sensitive Information - GXA, The Role of Encryption in Information Security: How Encryption Protects and also What is Data Encryption? - Bitdefender Cyberpedia. Here it is:
What Is Data Encryption? - Bitdefender Cyberpedia
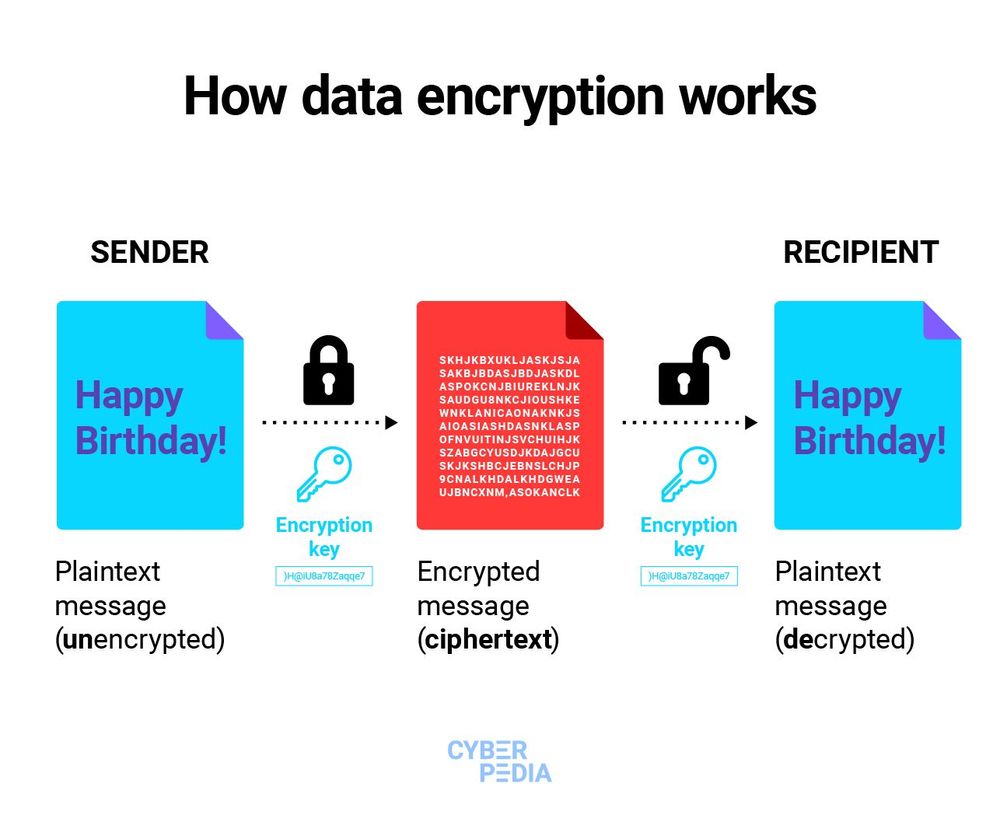 www.bitdefender.com
www.bitdefender.com
What Is Encryption? - Definition, Types & More | Proofpoint US
 www.proofpoint.com
www.proofpoint.com
encryption transition css opacity information definition proofpoint javatpoint transparent
Digital Signature Cryptography | Know 2 Major Forms Of Encryption
 www.educba.com
www.educba.com
signature digital cryptography security software network authentication development tutorials tutorial
What Is Data Encryption? - Bitdefender Cyberpedia
 www.bitdefender.com
www.bitdefender.com
The Role Of Encryption In Information Security: How Encryption Protects
 safebase.io
safebase.io
What Is Data Encryption? Types And Best Practices
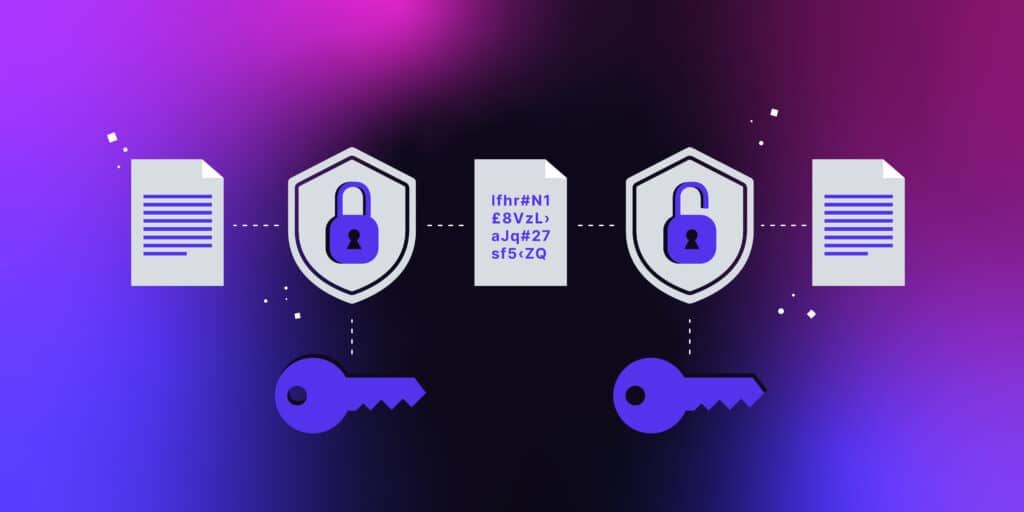 kinsta.com
kinsta.com
How To Use Encryption To Safeguard Data On Your Windows 10 Laptop
 www.computerworld.com
www.computerworld.com
encryption security data cybersecurity laptop safeguard ransomware cisco zoom concerns problems solves biggest eta one windows use national if charity
The Importance Of Cyber Security: How To Stay Safe In Today's Digital
 www.compuone.com
www.compuone.com
How To Protect Personal Information Online: A 15-step Guide | Norton
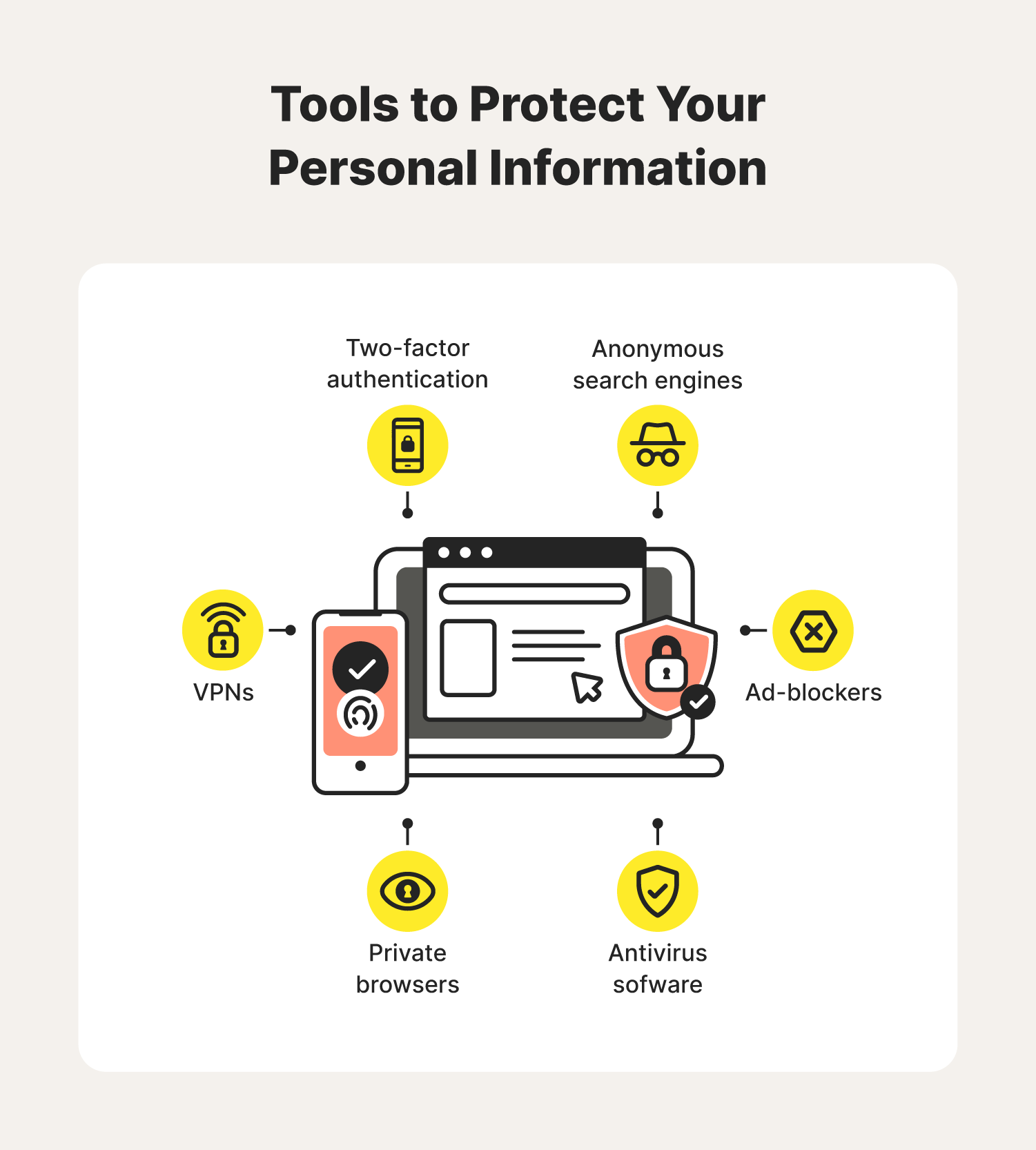 us.norton.com
us.norton.com
Cryptographic Keys 101: What They Are & How They Secure Data - Hashed
 www.thesslstore.com
www.thesslstore.com
11 Ways How To Protect Your Personal Information Online - PassCamp
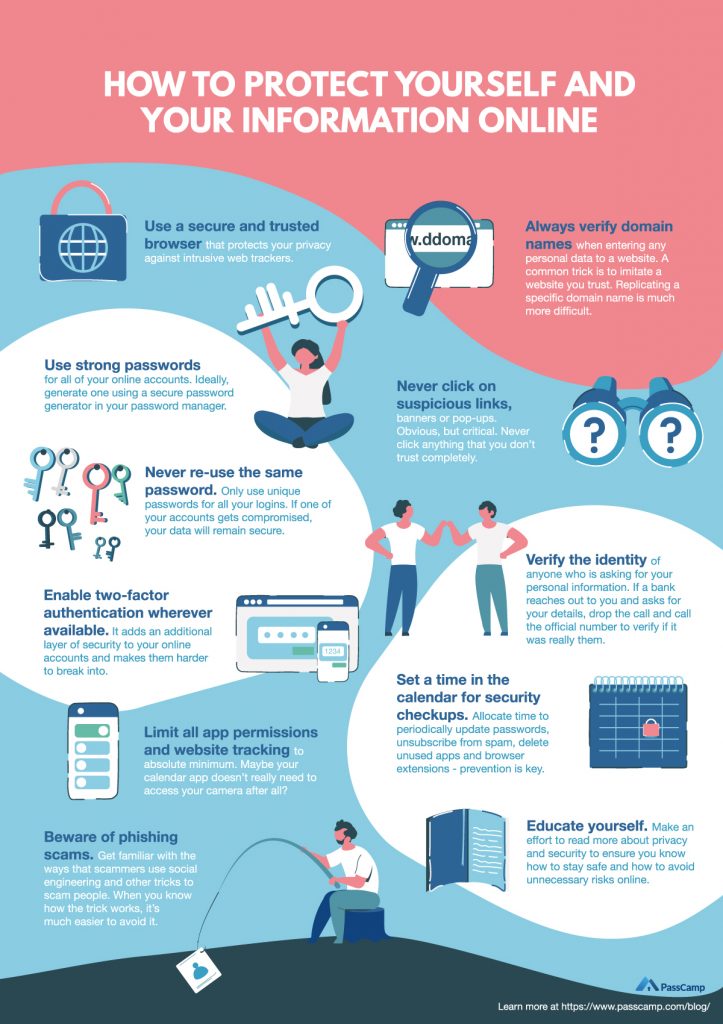 passcamp.com
passcamp.com
Safeguard Your Organization From Evolving Cyber Threats
 blog.techprognosis.com
blog.techprognosis.com
safeguard threats evolving organizations
What Is Encryption ? How Does It Work ? | Vednam
 vednam.com
vednam.com
encryption data what does level why work dataverse business field security information vital technology sensitive standard linkedin uses info need
Data Encryption: Safeguarding Sensitive Information - GXA
 gxait.com
gxait.com
What Is Encryption And How Does It Work?
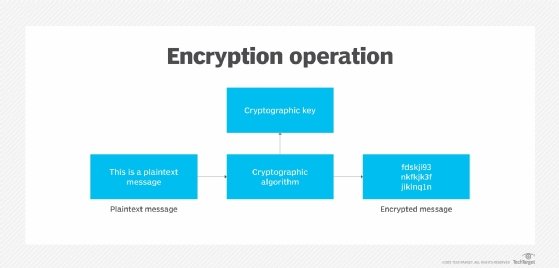 searchsecurity.techtarget.com
searchsecurity.techtarget.com
encryption definition security what example used operation does works keys benefits algorithms work
7 Ways To Safeguard Personal Data Online - The Video Ink
 thevideoink.com
thevideoink.com
Encryption: What Is It And How Does Encryption Software Work? | WIRED UK
 www.wired.co.uk
www.wired.co.uk
encryption ensure wired
What Is Sensitive Data? - Polymer
sensitive compliance
Encryption Choices: Rsa Vs. Aes Explained | Prey
 preyproject.com
preyproject.com
Sensitive Data And The GDPR: What You Need To Know
 gdprinformer.com
gdprinformer.com
sensitive data gdpr need know what personal articles processing
5 Types Of Vulnerability Scanning Tools For Cyber Security Best Practices
 www.thedigitalbridges.com
www.thedigitalbridges.com
scanning vulnerability cyber seguridad fortinet quadrant challenger gartner practices informationssicherheit política
Tips To Safeguard Sensitive Data
 malvern.bank
malvern.bank
Important Practices That Safeguard Your Business’ Cyber Security - CKAB
 ckab.com
ckab.com
cyber security safeguard practices important business 2020 performance data franchise sales
Sophos SafeGuard Encryption Synchronized Encryption Full Disk Encryption
 sophos.optrics.com
sophos.optrics.com
safeguard sophos encryption disk automatically everywhere protect data
What Is Data Encryption? Types And Best Practices
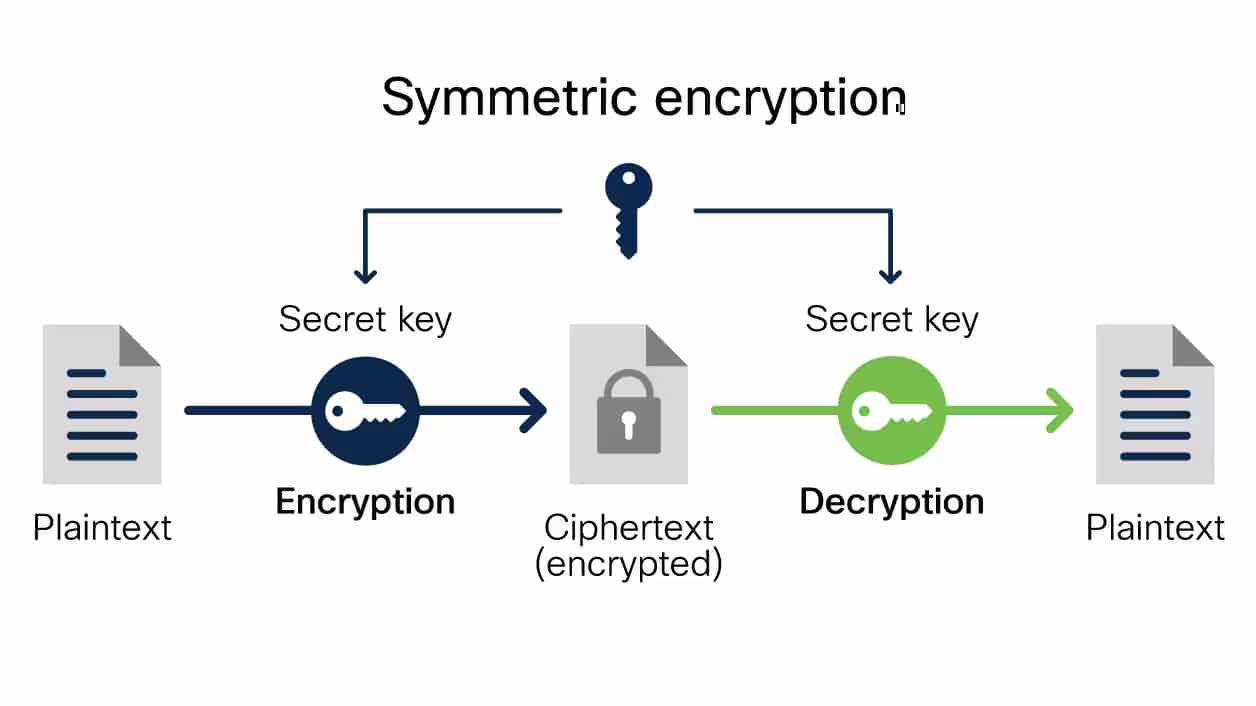 kinsta.com
kinsta.com
The importance of cyber security: how to stay safe in today's digital. Encryption definition security what example used operation does works keys benefits algorithms work. Tips to safeguard sensitive data